Abo ut
Methodological basis for the implementation of a solution for identity and authorization management
Whether an audit is just around the corner or a data leak has alarmed those responsible in management and IT - the need for action in terms of identity and authorization management arises quickly. However, it is much more difficult to reach agreement on the necessary measures and responsibilities. The IAM reference model from Peak Solution creates the prerequisites for quickly recognizing the weaknesses of the previous system in the company and enabling the basis for better management of authorizations. The model was originally developed for a large, international company in which the complexity of the authorization structures caused particular problems: The business-strategically designed, great independence of the business units meant that IT systems were operated centrally, but decentralized and very individually via authorizations was decided.
Components of the IAM reference model
Authorization process (Entitlement), provision process (Provisioning), authorization organization (Rights Organization) and auditing (Auditing) are the four main components that have to be implemented organizationally and technically for a "clean" IAM. Processes must be defined for all four components. The associated process view enables what is often so difficult in complex contexts: the clear division of responsibilities.
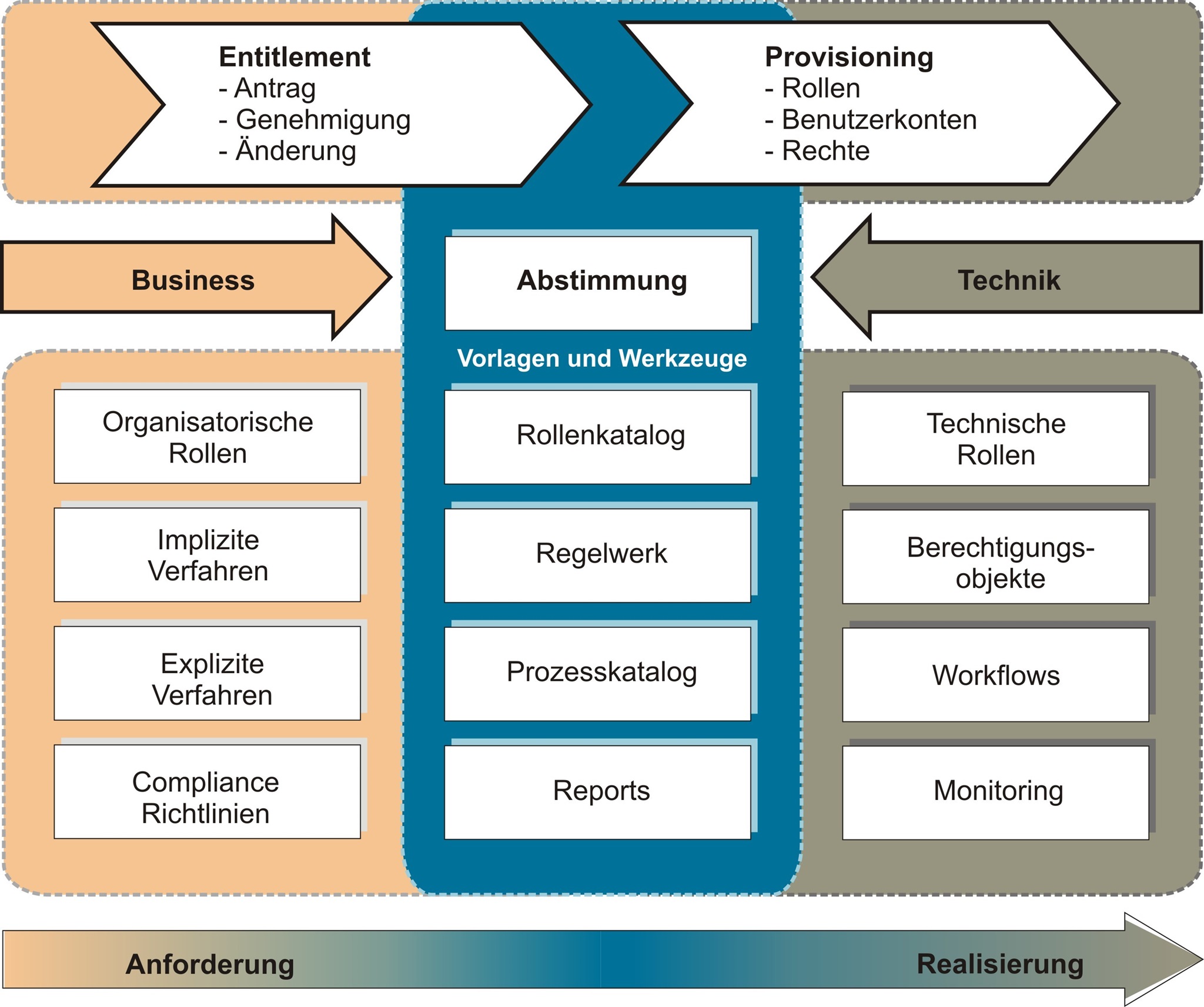
Figure 1: The IAM reference model offers templates and tools for planning, coordinating and documenting measures in the area of identity and access management.
Authorization process (Entitlement)
Every effective granting of system authorization or a system account must be preceded by an authorization process (Entitlement). A distinction is made between explicit procedures with application and approval and implicit procedures that run automatically according to rules. The set of rules refers to characteristics that describe people and are available in different IT systems. Prerequisite for the functioning of this procedure is the timely and high quality maintenance of the data.
The advantage of the implicit procedure is its efficiency and traceability. The disadvantage of the implicit procedure is that authorizations cannot be assigned individually. If rule-based processing is not possible or not desired due to approval or information requirements, approval must be given in accordance with the explicit procedure.
It is important that a process must also be defined for the explicit assignment so that the need for flexible authorization decisions does not lead to workarounds and rule violations. For this purpose, actors, responsibilities, procedural steps, control points and the flow of information must be defined. Since an explicit procedure is normally a supplement to automatic implicit procedures, an interface to the IAM system should be provided in any case. This means that provisioning can take place automatically, even if the approval was given “manually”.
Rights organization
The rights organization is the image of what is to be regulated in an organization. First of all, it is about the creation and maintenance of authorization objects and their definition with regard to authorization assignment.
An authorization object consists of resources and functions that can be used by a user after a successful authorization check. An authorization object can be a database table, for example, and the functions would be reading, changing existing entries, creating new entries or deleting them. The detailed definition and documentation of authorization objects is essential. This is the only way to correctly apply and understand authorization rules. It makes sense to consider authorization objects in the context of their life cycle. The following questions help to describe authorization objects in detail: Who created it? Who is responsible for that? When will it be deleted or what retention period must be observed? Which information protection class is necessary? Who can grant authorizations?
The other side of the rights organization is the definition of groups with equal rights. Technical advice from IT is appropriate here, but the definition of user groups is clearly a management task. This is where the actual rules are defined that will later allow the automated management of identities, accounts and authorizations. The assignment rules are based on roles that can be divided into three categories: organizational, functional and technical. Roles can be used in both an explicit and an implicit assignment of authorizations. The shape is only dependent on business needs. The advantage of role-based processing is better clarity and thus easier use in application processes.
Provisioning process
Once the authorization process and authorization organization have been defined, it is about the actual creation and assignment of authorizations in IT systems. How provisioning should be carried out in practice must be decided on the basis of the circumstances in an organization and on the basis of cost-benefit considerations. Assuming that the procedures and responsibilities would withstand a maturity analysis, fully automated user management in an IAM system would be the ideal solution. Provisioning is then carried out quickly, error-free and completely logged, and the administration costs are low. However, an automatic solution is only worthwhile for systems with many users who often need similar changes. Automatic provisioning stands or falls with the rules; adapting them can be very time-consuming.
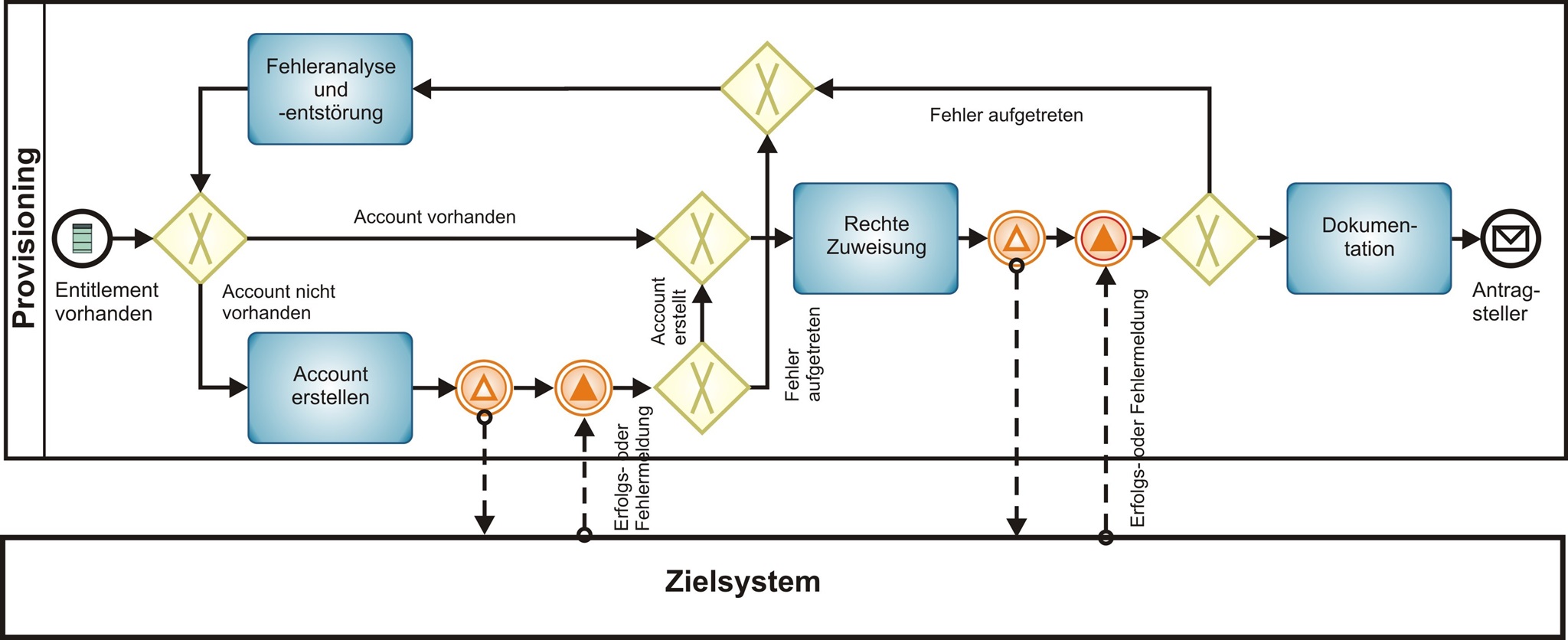
Figure 2: The process catalog of the IAM reference model defines generic processes for the assignment and provision of authorizations.
With the semi-automatic account and authorization provision, an account is automatically created in the target application at the end of a successful authorization process and, if necessary, given basic rights (e.g. group membership, system role). The necessary further processing then takes place manually (e.g. moving to an organizational unit, extension of authorizations, creation of user directories). The disadvantage is that manual (and error-prone) interventions are necessary, which increases the administrative effort. You also have to ensure that manual interventions are logged. A very important advantage of the automation is already given: the possible automatic deactivation of accounts, for example when an employee leaves.
Purely manual provision is even more flexible and easier to expand than semi-automatic provision. It should be mentioned for the sake of completeness, because in principle accounts and rights can also be set up directly in the target systems with on-board resources. Such a solution is complex to administer, difficult to maintain and prone to errors. In general, however, it is also possible in this case to adequately deal with security requirements if a fully traceable, documented provisioning and deprovisioning process is adhered to.
Auditing
Review processes are necessary for the continuous, systematic review of the correctness of the assigned authorizations. This is done by regularly checking the assigned rights on the basis of reports by those responsible, such as cost center managers, supervisors, contract owners. This ensures that authorizations that are no longer required are deleted and incorrect settings are corrected. Those responsible must always have an overview of the current authorization situation. The processes for creating an authorization organization, for assigning authorizations and for effectively setting up authorizations are all accompanied by consistent documentation. In the fourth module it must be determined how the other three are to be checked and where the competencies and responsibilities lie. For example, the time intervals and the need for checking can be made dependent on the protection class of the information stored. Control and evaluation of the effective authorizations and their derivation ensure that the question can be answered at any time: Who had when, where, what authorization and why?
Conclusion:
The proposed IAM reference model with a process view distributed over four components is recommended in order to ensure transparency and traceability right from the start. Even if the technical implementation only progresses step by step or the automation in areas proves to be too complex: The model makes it easier to assign responsibility and gives management and IT departments, for example, a common frame of reference. In particular, the clear separation of Entitlement, Provisioning and Rights Organization makes it possible to assign responsibilities and tasks even in organizations in which many departments have a say in security issues. The clear basic concept and consistent documentation ensure that a company already has the upper hand in compliance and liability issues, even if the processes are still being set up.
