Design IAM solutions with PSS
The Peak Security Suite (PSS) is an IAM solution for identity access management (management of identity, ID and authorization data of employees, visitors for user management as well as external company management and external personnel). Our IAM system develops its full potential in the center between identity management, access management and physical access control. In this way, physical and logical security requirements are closely linked.
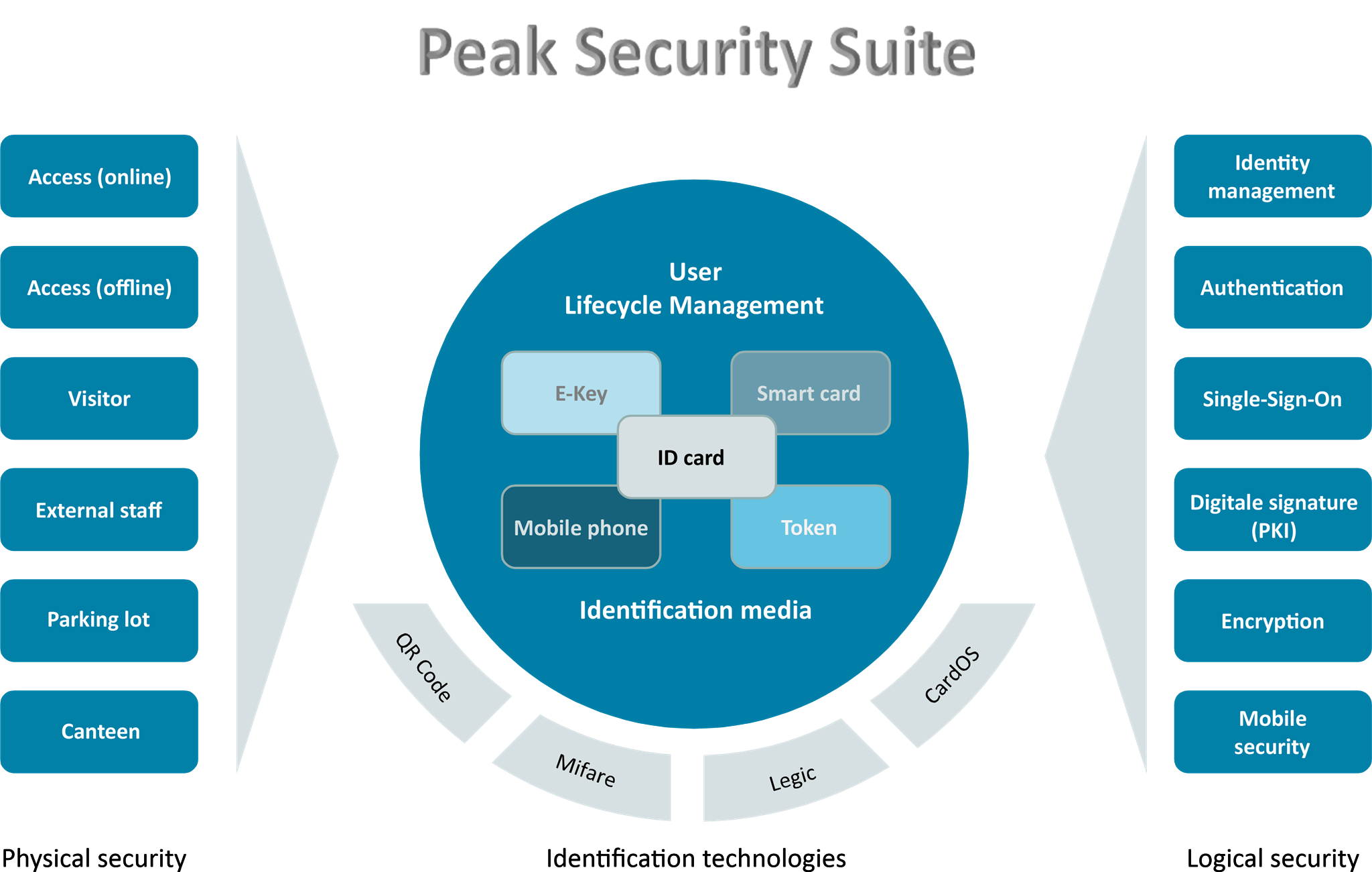
The multifunctional company ID card and other media (e.g. tokens, mobile devices such as smartphones, electronic keys, etc.), including the associated identification technologies (e.g. RFID, digital certificates, QR code, etc.), are centralized in the Peak Security Suite software managed. Standardized interfaces, e.g. based on LDAP, OCSP, SCEP, PKCS JSON, XML or REST, ensure automated data comparison between all connected (sub)systems.
Even complex use cases, such as Our IAM systems reliably cover problems that occur, for example, with operators of real estate and industrial properties.
IAM system for you - The features of the Peak Security Suite
 Scalability
Scalability
All parts of the Peak Security Suite can be scaled horizontally and vertically and thus optimized for any number of users. The necessary load balancing takes place automatically.
 Expandability
Expandability
Further solutions or customer-specific extensions can be added to the Peak Security Suite at any time. The maintainability and upgradeability of the system remain unaffected.
 Cloud enabled
Cloud enabled
The Peak Security Suitecan be operated partially or completely in a cloud infrastructure, e.g. based on Azure or AWS. Communication takes place via a secure exchange of messages.
 Integration ability
Integration ability
Peak Security Suite is completely REST-based. By that the entire program logic can be integrated into existing processes and applications without the need for an additional GUI.
 Platform independent
Platform independent
Peak Security Suite is largely independent of certain system platforms. The only required runtime environment is a Docker infrastructure in which the relevant containers are started.
 Investment protection
Investment protection
The modular structure of the system based on microservices ensures that individual parts of the Peak Security Suite or the entire system can be quickly adapted to new IT requirements.
What makes our Identity and Access Management special?

Administration of user identities
In the Peak Security Suite, the identities of employees, visitors and external personnel are brought together in an IAM system and managed centrally. Standardized, bidirectional connectors enable the synchronization of identity data with existing directory services (e.g. Active Directory, eDirectory), identity management systems (e.g. NetIQ, One Identiy Manager) and/or human resources management systems (e.g. SAP HR).
Access control with RFID and the creation of ID cards
The Peak Security Suite offers functions for the professional creation of RFID ID cards - from image capture and printing to coding and personalization. All common encodings are supported by our IAM system (e.g. LEGIC, LEGIC Advant, MIFARE® Classic, MIFARE® Desfire, HDI, etc.). The tools from various manufacturers (e.g. hardware such as ID printers, coding devices, etc.) are easily connected via the Peak Smart Bridge.


Visitor management
Complex visitor processes are implemented in a GDPR-compliant manner with the Peak Security Suite. User-friendly functions enable, among other things, the pre-registration of visitors, their check-in at reception as well as the production and issuing of visitor passes, also with individual assignment of special access and usage rights. Even registering multi-day and/or recurring visits and managing visitor groups is no problem for the Peak Security Suite.
Self Souvereign Identity & Self Services
With the help of cloud-enabled user self-services, employees, visitors and external staff can apply for proof of identity and authorizations. This also includes the activation of additional services, such as the use of WiFi, access to a conference room or a visit to the company canteen. In the background, workflow-based application and approval processes ensure the necessary security and compliance in the company.


The access control system for you: Our integration platform
The Peak Security Suite integrates various access control systems (and electronic locking systems) across locations in one IAM system. Special connectors, which are precisely tailored and optimized to the functions and security requirements of the respective access control systems (e.g. dormakaba, Primion, Interflex, nedap, and others), regulate the synchronization and provisioning of room zones, authorization profiles and identity data between the connected systems. Central administration and fully automatic assignment and revocation of access authorizations ensure a significant reduction in maintenance effort.
Read here "Peak Security Suite - The smart addition for your access control system".
Smart Card Management: Our management of chip cards and digital certificates (PKI)
Multifunctional employee ID cards (= chip cards, smart cards) usually contain digital X.509 certificates with which certain characteristics of a person are confirmed and their authenticity and integrity are checked using cryptographic processes. To issue such certificates, the Peak Security Suite is connected to an existing certification authority (= CA, Certificate Authority) - such as the Microsoft PKI. The application then ensures that the provided certificates are correctly attached to the smart card chip of the ID card and stored securely in a certificate store (e.g. Windows Cert Store / AD). The Peak Security Suite also offers a range of functions for managing smart cards and digital certificates. In addition to notification services, this includes extending, renewing and revoking certificates, resetting forgotten or blocked PINs and restoring keys.


Sign on your mobile phone: The integration of mobile devices
As an alternative to conventional RFID and chip cards, Peak Security Suite can also manage mobile devices as a medium for storing identity and authorization credentials. Companies can take advantage of this and conveniently integrate the processes for managing the smart devices of different groups of people into the existing physical and logical security systems.
Lifecycle management for ID media
The life cycle of identities and ID media includes, for example, the initial creation, personalization and issuing of ID cards, the provision of digital certificates and tokens, the handling of replacement cards, the blocking, renewal and withdrawal of login information and much more. Peak Security Suite ensures that all phases in the life cycle are managed reliably compliant.


Rights management workflows and rule-based processing
Within Peak Security Suite, customizable workflows and rules ensure that all the necessary process steps for applying, approving and provisioning of identity and authorizations credentials are seamlessly integrated and implemented across systems. This also includes the automatic consideration of approval requirements already in the application process (e.g. security and reliability checks, training courses, instructions, comparison with black and prohibited lists, etc.) as well as the monitoring of deadlines and dates. With the help of the workflow editor and designer, the existing workflows can be adapted or expanded at any time.
Digital wallets & passbooks for managing QR codes
Digital wallets or a passbook act as digital ID in the visitor management of the Peak Security Suite. Like a digital boarding pass, it shows the user the date, time, contact person and location of their visit. A parking space, for example, can also be entered as a location in order to guide the visitor efficiently. On the other hand, the QR code in the wallet/passbook enables the visitor to be automatically identified by reception. If the technical basics are in place, the QR code can also be used for physical access.


Contractor management
External companies independently register the employees they employ via the Peak Security Suite and maintain their data. In return, the respective company receives one or more user accounts with limited administrative rights. For example, there is the option of applying for a service provider ID card with special authorizations, which is then approved and produced via the Peak Security Suite. A function similar to visitor registration is also available for short-term assignments. An external company is created in the Peak Security Suite using a special onboarding process.
Reporting
A comprehensive catalog of evaluations relating to the managed identities, ID media and authorizations is already integrated in the Peak Security Suite. Further reports can be supplemented and adapted if necessary.

Contact and further information
Please feel free to contact us by phone or email. Here you can find more information about the basics, capabilities and possible uses of the Peak Security Suite:



